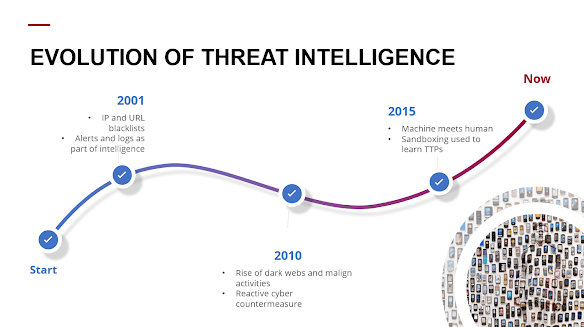
Threat Intelligence keeps evolving for the past 22 years. Let's walk through the historical timeline of threat intelligence.
2001
The precursors to threat intelligence began to emerge at this time. IP and URL blacklists were the first to appear. Security software such as Security Information and Event Management (SIEM) systems and next-generation firewalls (NGFWs) utilized blacklists to generate alerts and reports. Security analysts manually scanned for threats and delivered daily customer updates. Most cyberattacks are network-based attacks. In the same year, The National Cyber Security Alliance (NCSA) is established in response to the September 11 assaults on the World Trade Center as part of a cybersecurity initiative between industry leaders and government stakeholders.
2010
The dark web and malicious activities were exploding, revealing the limitations of the security software of the time, which was not designed to process the number of Indicators of Compromise that were raining down like a frog swarm. They were incapable of identifying and processing the dust storms of malicious domains, IPs, and other hazards.
The industry of cybersecurity responded. Machine learning and artificial intelligence (AI) have the potential to automate and correlate data on a much larger scale. With millions of sensors deployed across continents, oceans of data have been accumulated. Using big data technologies, they processed and analyzed it. These systems were subsequently employed to execute complex detection across all attack surfaces. In addition, big data technology spawned the concept of threat intelligence.
Stuxnet was a case involving a virus that made international headlines. Does anyone here recall Operation Aurora occurring in the same year? Few Internet consumers are aware that even the mighty Google has had its backend infrastructure compromised. It was part of a series of attacks that became known as Operation Aurora -- a coordinated hacking campaign conducted by the Chinese government's military hackers against some of the world's largest companies at the time, including Adobe, Rackspace, Juniper, Yahoo, Symantec, Northrop Grumman, Morgan Stanley, and others. The actual assaults occurred in the 2000s, but they did not become public knowledge until early 2010.
Google's history was reshaped by Operation Aurora. After discovering and disclosing the intrusions, Google decided to stop collaborating with the Chinese government to censor search results for Google.cn, and the company subsequently ceased operations in China. The Operation Aurora cyberattack was specifically cited as one of the motives for Google's decision.
2015
Threat intelligence has again evolved. This big data technology generated far too many false alarms. Cybersecurity required its personnel. Experts in security who supervise intelligence collection could reduce false positives and better identify threats and attack methods unique to their organizations. It meant quicker detection and response, as well as a refocus on identifying and prioritizing vulnerabilities.
Now
In 2018, the market for threat intelligence exploded. Hundreds of new businesses with a concentration on data quality have emerged, offering specialized services. The objective was to provide decision and action guidelines. The businesses that purchased threat intelligence products and services began to utilize them more effectively, such as by modifying their data collection to meet security requirements.
And beyond the year 2023? Still, the market is expanding. By 2023, threat intelligence may be worth 13 billion dollars, according to recent studies. Threat intelligence is being implemented by increasingly diminutive organizations.
This will be a new era of cooperation in the primary. Cybersecurity companies are already integrating their products and services with those of others in an effort to become more comprehensive.
The nature of cybersecurity will shift from reactive to proactive, and the function of security teams within organizations will expand. They will interact more with all business segments and groups. They will be responsible for providing proactive threat intelligence that not only protects, but also identifies risk and shapes business objectives. Threat intelligence will effectively predict and prevent assaults at the earliest stage, and sooner or later will underpin the entire concept of proactive cybersecurity and organizational risk.



Post a Comment
0Comments