The term "dark web" refers to the bottom-most and deepest layer of the internet, which is not indexed by search engines and whose contents are not visible to regular browsers and users. Individuals have to utilize specialized browsers like Tor, which offer users anonymity and protect their data, in order to access the Dark Web. Criminals undertake a variety of illicit operations on the dark web due to the anonymity provided to users.
The web is divided into three layers:
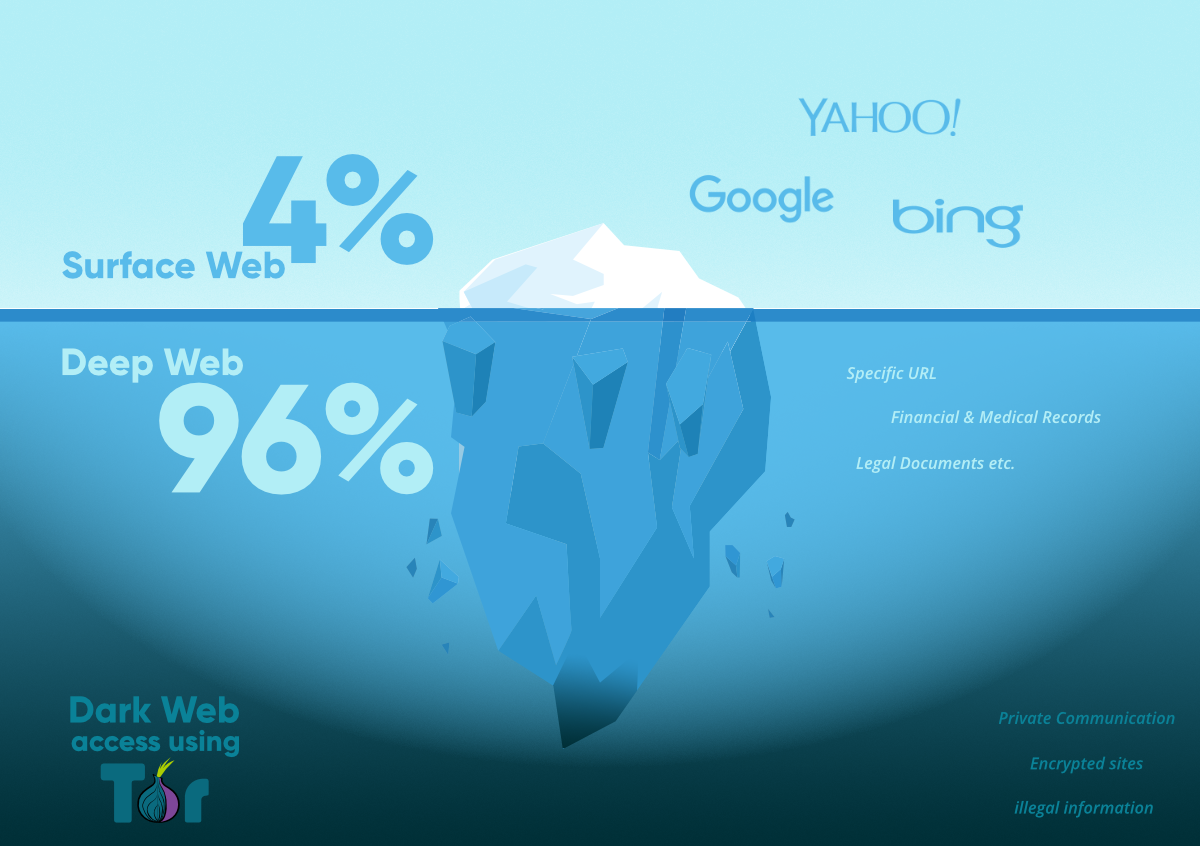
1. Surface Web
The surface web, which is the top layer, contains content that is accessible and indexed by search engines like Google, Yahoo, and Bing. Access to open websites like Wikipedia, eBay, Facebook, and YouTube is simple from the surface web. Only 4% of the web overall is made up of the surface web.
2. Deep Web
Because its contents are not indexed by search engines, this layer of the web is inaccessible to regular users. The deep web's contents can only be viewed by a person who has the proper authorization. The deep web may contain information related to the military, organization confidentiality, legal files, financial records, medical records, records of governmental agencies, and subscription information.
3. Dark Web
The third and deepest layer of the web is known as the "dark web." It is a portion of the internet that cannot be seen or reached without using a certain web browser, such as the Tor browser, which safeguards users' anonymity. It is employed to engage in illegal and antisocial behavior. The dark web uses encryption to give users complete anonymity and is not indexed by search engines. The dark web is used by cybercriminals to carry out evil deeds like drug trafficking, anti-social campaigns, and the usage of cryptocurrencies for illicit transactions.
So this brings us to the question "why you need to monitor dark web?" Three reasons why you need to monitor the Dark Web:
- Finding Data Breach - To identify the stolen credentials and other personal information that has been distributed on the dark web networks, a sophisticated piece of software is essential. You can configure your queries on the dark web monitoring tool to find any pertinent data or information. They constantly scan the open, dark, and deep web, then pass these searches via AI algorithms to determine which are pertinent. In order to attain a better outcome, we later send a person to conduct additional information screening.
- Detecting Physical Threats Against People and Assets - The main draw for criminals to the dark web is that all users must use an encrypted browser to access it, making their presence absolutely anonymous. This means that criminals can and do brag about their actions or use them as a component of their plans. You may continuously watch the dark web with dark web monitoring, and you will be alerted as soon as a criminal talks or potentially compromises one of your employees or resources.
- Predicting Potential Terrorist Attacks - Companies monitor online threats to them for physical threats; in addition, the dark web is where terrorists go to coordinate, plan, and launch attacks. By monitoring the Dark Web, the companies can join their discussion and use the information gathered to potentially anticipate and identify terrorist threats that have been made against the company.
Many vendors are currently offering Dark Web monitoring services, but there is still a widespread misunderstanding about how they operate or even if they operate at all. The Dark Web monitoring tool does not filter the entirety of the dark web because doing so would be difficult and they could not begin taking down against stolen data or legally obtained property. There is frequently nothing you can do to prevent something from being sold or used improperly once it ends up on an underground commercial center.
Only publicly accessible content can be screened by the Dark Web Monitoring. Dark web scanners are unable to access content that is shielded from scraping tools, much like how search engine crawlers cannot see content that has hidden itself behind a login or barrier. Instead, they are focusing their attention on huge data dumps that contain compromised personal information like credentials and passwords.



Post a Comment
0Comments